Exim Configuration Manager
- Log in to your whm>>service configeration>>Exim Configuration Manager
You can find these configurations in the Exim Configuration Manager located in the Service Configuration category. This guide is intended for Host winds clients with a Cloud VPS or Dedicated Server with a cPanel license and access to WHM.
Basic Editor
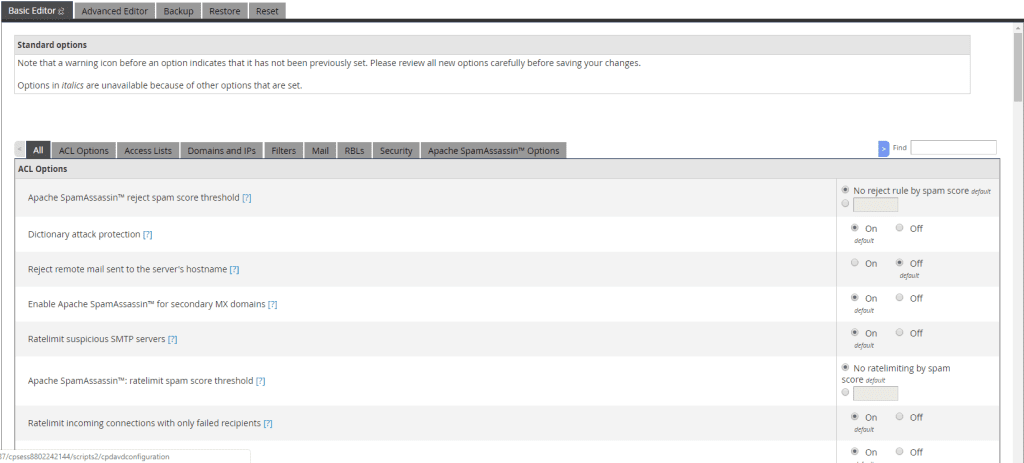

ACL Options
- Apache Spam Assassin rejects spam score threshold: Specifies the Spam Assassin score threshold a mail must be detected for it to be rejected at SMTP time. It can also be disabled.
- Dictionary attack protection: Drops and rate limits hosts with more than 4 failed recipients to prevent dictionary attacks.
- Reject remote mail sent to the server’s hostname: Specifies whether or not to reject mail at SMTP time if the recipient’s address is to the server’s hostname.
- Enable Apache Spam Assassin for secondary MX domains: Specifies whether mail sent to the primary mail exchanger for domains listed within the secondary MX list will also be scanned with Apache Spam Assassin.
- Rate limit suspicious SMTP servers: Specifies whether to ratel imit incoming SMTP connections from hosts that have previously attacked this server, have been recently matched on a mailing blacklist (RBLs) or did not set QUIT with the connection.
- Apache Spam Assassin: rate limit spam score threshold: Specifies a spam score threshold for mail sent in from hosts to enable rate limiting on those hosts.
- Rate limit incoming connections with only failed recipients: Specifies whether to enable rate limiting on incoming SMTP connections that have only been sent to failed recipients five separate times within the past hour.
- Require HELO before MAIL: Specifies whether incoming SMTP connections are required to send HELO before MAIL.
- Introduce a delay into the SMTP transaction for unknown hosts and messages detected as spam: Specifies whether the SMTP receiver should wait additional seconds to connect when the inbound messages are detected as spam.
- Do not delay the SMTP connections for hosts in the Grey listing “Trusted Hosts” list: Specifies whether hosts listed as “trusted hosts” in the grey list should be exempt from introducing delays to the SMTP connection.
- Do not delay the SMTP connections for hosts in the Grey listing “Common Mail Providers” list: Specifies whether hosts listed as “common mail providers” in the grey list should be exempt from introducing delays to the SMTP connection.
- Require remote (hostname/IP address) HELO: Specifies whether incoming SMTP connections are required to send a HELO that does not match the primary hostname or local IP.
- Require remote (domain) HELO: Specifies whether incoming SMTP connections are required to send a HELO that does not match the server’s local domains.
- Require RFC-compliant HELO: Specifies whether incoming SMTP connections are required to send a HELO following internet standard format (RFC2821 4.1.1.1).
- Allow DKIM verification for incoming messages: Specifies whether Exim should verify the signature of incoming mail, even if Exim is not configured to act upon the verification results.
- Reject DKIM failures: Specifies whether or not to reject mail at SMTP time if the DKIM signature of the sender fails validation. Requires Allow DKIM verification for incoming messages to be enabled.
- Maximum message recipients (soft limit): Specifies the limit for the number of recipients a single message can have before rejecting recipient addresses.
- Before disconnecting (hard limit), maximum message recipients specify the number of recipients a single message can have before disconnecting and rate limiting the connection.


Access Lists
- Automatically whitelist known mobile device providers: Specifies whether hosts specified within the known mail providers file are automatically whitelisted.
- Blacklisted SMTP IP Addresses: Lists and allows editing of the IP addresses of SMTP hosts that are blacklisted.
- Sender verification bypass IP Addresses: Specifies the IPs that bypass the SMTP-time sender verification checks.
- Only-verify-recipient: Specifies hosts or IPs exempt from spam checks at SMTP time, except for recipient verification.
- Trusted SMTP IP Addresses: Specifies IP addresses exempt from all SMTP sender, recipient, spam, and relaying checks.
- Backup MX Hosts: Specifies hosts with rDNS where connections are allowed regardless of rate limits.
- Trusted mail users: Specifies users on the server that may set the ‘From:’ header to any value when Rewrite From header to match actual sender is enabled.
Domains and IPs
- Send mail from the account’s IP address: Specifies whether to use the account’s IPv4 address for outgoing mail rather than the server’s default IP.
- Reference /etc/mail helo for custom outgoing SMTP HELO: Specifies whether to send HELO based on the domain listed in /etc/mail helo.
- Reference /etc/mailips for custom IP on outgoing SMTP connections: Specifies whether to send outgoing mail from the IP that matches the domain listed in /etc/ mailips.
Filters
- System Filter File: Specifies the location for the system filter file.
- Attachments: Filter messages with dangerous attachments: Specifies whether or not to filter mail with dangerous attachments.
- Apache SpamAssassin: Global Subject Rewrite: Specifies whether or not to prefix the ‘X-Spam-Subject’ header prefix onto the ‘Subject’ header and omits the ‘X-Spam-Subject’ header.
- Apache Spam Assassin: bounce spam score threshold: Specifies the spam score threshold for the server to bounce mail scored above this value.
- Apache Spam Assassin: X-Spam-Subject/Subject header prefix for spam emails: Specifies the text to prefix either the ‘X-Spam-Subject’ or ‘Subject’ headers for messages that Apache Spam Assassin marks as spam.
- Log sender rates in the exim main log: Specifies whether or not to include sender rates in the exim mainlog.
- Sender Verification Callouts: Specifies whether to verify the existence of email senders with callouts.
- Smarthost support: Specifies the route_list entry for sending outgoing messages with a smarthost.
- Rewrite From: header to match actual sender: Specifies whether the From: header will be rewritten to match the address of the actual message sender.
- Send generic recipient failure messages: Specifies whether to display “The recipient cannot be verified. Please check all recipients of this message to verify they are valid.” message instead of a specific reason why sending mail to a recipient would fail.
- Allow mail delivery if malware scanner fails: Specifies whether or not to defer mail if the virus/malware scanner fails.
- Sender Verification: Specifies whether to validate the domain a mail reports as its origin actually exists.
- Set SMTP Sender: headers: Specifies whether to set the Sender: header as the account used for SMTP login.
- Allow mail delivery if spam scanner fails: Specifies whether or not to defer mail if the spam scanner fails.
- Enable Sender Rewriting Scheme (SRS) Support: Specifies whether to enable support for rewriting the sender address such that the email appears to come from the forwarding mail server.
- Query Apache server status to determine the sender of email sent from processes running as nobody: Specifies whether cPanel will query the webserver to determine the sender if the X-PHP-Script headers are not available.
- Trust X-PHP-Script headers to determine the sender of email sent from processes running as nobody: Specifies whether cPanel will use the X-PHP-Script headers to determine a message for email archiving and limits if the MailHeaders patch is installed in EasyApache.
- Hosts to which to advertise the SMTP DSN option: Specifies the hosts to which SMTP DSN support is advertised.
- Hosts to which to advertise the SMTPUTF8 SMTP option: Specifies the hosts to which SMTPUTF8 support is advertised.
RBLs
- Manage Custom RBLs: Specifies custom RBLs the server will use to reject mail at SMTP time.
- RBL: bl.spamcop.net: Specifies whether to use the bl.spamcop.net RBL to reject mail at SMTP time.
- RBL: zen.spamhaus.org: Specifies whether to use the zen.spamhaus.org RBL to reject mail at SMTP time.
- Exempt servers in the same netblocks as this one from RBL checks: Specifies whether or not servers listed in the same IANA netblock are subject to RBL checks.
- Exempt servers in the Grey listing “Common Mail Providers” list from RBL checks: Specifies whether or not to run RBL checks on mail from IP address blocks listed in the Greylisting “Common Mail Providers” list.
- Exempt servers in the Grey listing “Trusted Hosts” list from RBL checks: Specifies whether or not to run RBL checks on mail from IP address blocks listed in the Grey listing “Trusted Hosts” list.
- Whitelist: IP addresses that should not be checked against RBLs: Specifies a custom list of IP addresses for which mail sent from them should not have RBL checks run against them.
Security
- Allow weak SSL/TLS ciphers: Specifies whether or not weak SSL/TLS ciphers are allowed.
- Require clients to connect with SSL or issue the STARTTLS command before they are allowed to authenticate with the server: Specifies whether or not authentication credentials are required to use SSL/TLS.
- Scan messages for malware from authenticated senders (exiscan): Specifies whether messages from authenticated senders are scanned using the Clam AV connector plugin.
- Scan outgoing messages for malware: Specifies whether outgoing messages should be scanned for malware using the Clam AV connector plugin, rejecting those testing positive.
- Options for OpenSSL: Specifies the SSL/TLS protocol configuration for OpenSSL.
- SSL/TLS Cipher Suite List: Specifies the supported SSL/TLS ciphers.
Apache Spam Assassin Options
- Apache Spam Assassin: Forced Global ON: Specifies whether Apache Spam Assassin is enabled for all accounts.
- Apache Spam Assassin: message size threshold to scan: Specifies the maximum size in KB a message can be for Spam Assassin to scan it.
- Scan outgoing messages for spam and reject based on the Apache Spam Assassin internal spam_ score setting: Specifies whether Apache Spam Assassin should scan outgoing mail for spam and reject those that test positive.
- Scan outgoing messages for spam and reject based on defined Apache Spam Assassin score: Specifies the minimum SpamAssassin score a scanned outgoing mail is determined to be to be rejected.
- Do not forward mail to external recipients if it matches the Apache Spam Assassin internal spam_ score setting: Specifies whether Apache Spam Assassin must be enabled, either per-user or globally, to allow outbound forwarding.
- Do not forward mail to external recipients based on the defined Apache Spam Assassin score: Specifies the spam score a message cannot exceed when Spam Assassin is enabled, either per-user or globally, to allow outbound forwarding.
- Enable BAYES_POISON_DEFENSE Apache Spam Assassin ruleset: Specifies whether to increase the score thresholds needed for bayes to learn HAM and SPAM to reduce the effectiveness of bayes poisoning used by spammers.
- Enable Passive OS Fingerprinting for Apache SpamAssassin: Specifies whether to enable OS fingerprinting to be used by SpamAssassin passively.
- Enable KAM Apache SpamAssassin ruleset: Specifies whether SpamAssassin uses the KAM ruleset.
- Enable the Apache SpamAssassin ruleset that cPanel uses on cpanel.net: Specifies whether to use rules for SpamAssassin from SPAM detected commonly at cpanel.net.
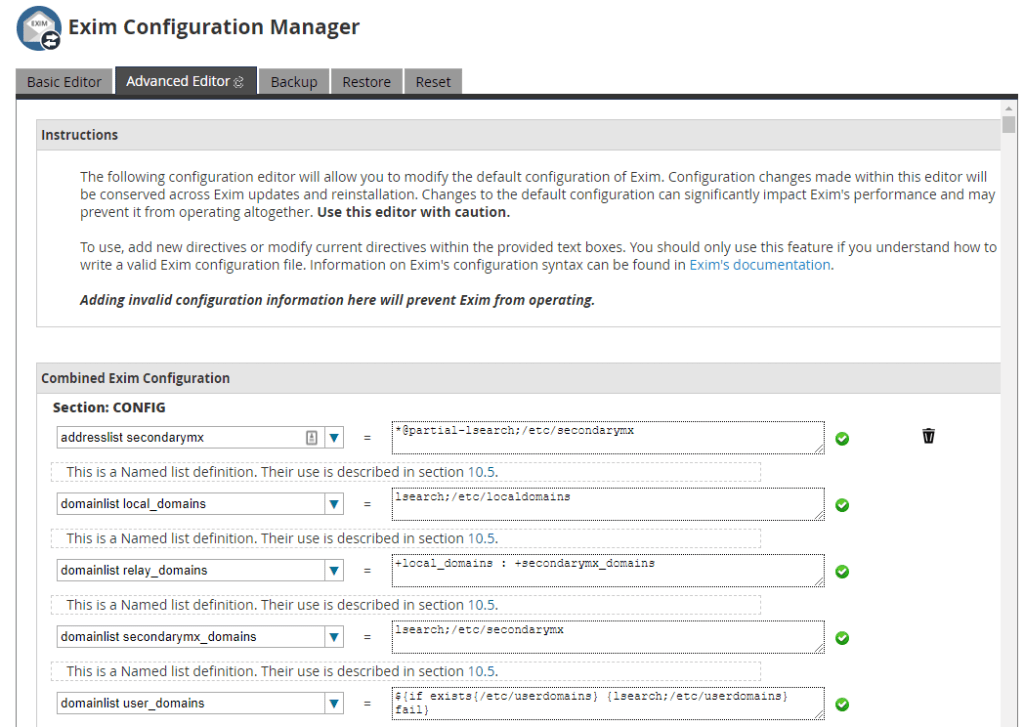
Advanced Editor
The Advanced Editor gives every variable and flag within the exim configuration files, allowing you to type in your own values for each entry.
It is recommended to stick with the Basic Editor to avoid accidentally breaking the Exim configuration with incorrectly inputted values in the Advanced Editor.
Backup
The Backup tab lets you save copies of your Exim configuration either to the server itself or as a download to your local computer.
Restore
The Restore tab lets you restore the Exim configuration from a backup generated under the Backup tab.
You can either upload a backup file from your local computer, or any backups saved on the server will appear in a table below the upload option. Any backups already on the server will give you a ‘Restore’ link to restore the configuration to that backup.
Reset
The Reset tab will let you reset the Exim configuration to a default configuration. You are given the option to specify what parts of the configuration you wish to reset, so you do not need to reset everything.